Introduction
This blog post is meant to accompany a talk titled “SaaS Security Basics on a Shoestring Budget.”
The talk shares my perspective as a recent founder who has spent a lot of the last year helping other founders with their security. Over that time I’ve come to realise that there is a lot of mystery and basic knowledge gap when it comes to keeping your product and infrastructure secure that the average technical founder or small team simply doesn’t have a grasp on.
Authentication
Password Managers
| Info | Advice |
|---|---|
 |  |
A password manager is a software tool that helps individuals and organizations securely store and manage their passwords. It acts as a vault for storing passwords and generates strong, unique passwords for each account. Some benefits of using a password manager include:
- Enhanced security: Password managers help create strong, unique passwords for every account, reducing the risk of password reuse and making it harder for attackers to guess or crack passwords.
- Simplified password management: With a password manager, users don’t need to remember multiple complex passwords. They can securely store and auto-fill passwords across different devices and platforms.
Actionable steps:
- Choose a reputable password manager: Research and select a password manager that fits your needs and has a good track record for security.
- Set a strong master password: Your master password is the key to access all your stored passwords, so it should be unique, long, and complex.
- Enable multi-factor authentication: Add an extra layer of security by enabling multi-factor authentication (MFA) for your password manager.
Links:
MFA
MFA stands for Multi-Factor Authentication, a security measure that adds an extra layer of protection to the authentication process by requiring users to provide multiple forms of verification to access a system or an account. MFA helps prevent unauthorized access and strengthens the security of sensitive information.
Benefits of MFA:
- Increases security: By requiring multiple factors of authentication, MFA significantly reduces the risk of unauthorized access to accounts or systems.
- Mitigates password-related risks: MFA reduces the reliance on passwords alone, which are often weak or easily compromised, making it difficult for attackers to gain access.
Actionable Steps:
- Enable MFA: Activate multi-factor authentication on all critical accounts and systems that offer this feature.
- Use different factors: Utilize a combination of factors such as hardware tokens and or one-time passwords for enhanced security.
- Keep backups: Ensuring offline or other forms of backups are made when only utilizing a single MFA favtor.
Links: -Multi-Factor Authentication Cheat Sheet
Leaked Passwords
Breached or leaked password monitoring is a process that allows individuals and organizations to check if their passwords have been exposed or compromised in data breaches. This can help increase the security of online accounts and systems by identifying weak or compromised passwords.
Benefits:
- Enhanced security: Breached password checking helps identify if passwords have been compromised, allowing users to take appropriate action to protect their accounts.
- Proactive approach: Checking for breached passwords allows individuals and organizations to be proactive in their security measures, reducing the risk of unauthorized access.
Actionable steps:
- Use reputable breached password checking tools, such as Have I Been Pwned or Firefox Monitor, to check if your passwords have been compromised.
- Prevent users with known breached password from reusing them, educate users on the importance of password managers.
Links:
Email Security
| Info | Advice |
|---|---|
 |  |
SPF
SPF (Sender Policy Framework) is an email authentication protocol that helps prevent email spoofing and phishing attacks. It allows email recipients to check if the sender is authorized to send emails on behalf of the claimed domain.
Benefits of SPF:
- Protection against email spoofing and sender address forgery
- Helps improve email deliverability
Actionable steps:
- Add SPF records to your DNS configuration, specifying the authorized mail servers for your domain
- Regularly monitor SPF failures and investigate any unauthorized sources of email using your domain
Links:
DKIM
DomainKeys Identified Mail (DKIM) is an email authentication method that allows the recipient of an email to verify that it came from the domain it claims to be from and that it hasn’t been modified during transit.
Benefits of DKIM:
- Protection against email spoofing and sender address forgery
- Enhances email deliverability
Actionable steps for implementing DKIM:
- Generate a public-private key pair for your domain.
- Publish the public key in your domain’s DNS records.
- Configure your email server to sign outgoing messages with the private key.
Links:
DMARC
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is another email authentication protocol that helps protect against email spoofing and phishing attacks. It allows organizations to specify how their emails should be handled when received by the recipients server and can help provide better visibility and control over email authentication in order to safeguard your domain from unauthorized use.
Benefits of DMARC:
- Further reduces the risk of email spoofing and phishing attacks by authenticating emails sent from a specific domain.
- Provides visibility into email fraud attempts and receiving reports on email deliverability.
Actionable steps to implement DMARC:
- Begin by publishing a DMARC record in your organization’s DNS settings.
- Gradually configure the DMARC policy to specify how to handle emails that fail authentication, such as quarantine or reject.
- Regularly review DMARC reports to ensure proper email authentication and address any potential issues.
Links:
Limiting attack surface
| Info | Advice |
|---|---|
 |  |
Identifying subdomains
Subdomain enumeration is the process of discovering and mapping out all the subdomains associated with a particular domain. By doing so, organizations can effectively limit their attack surface by identifying and securing these potentially vulnerable entry points into their network.
Benefits:
- Improved visibility: Identifying subdomains allows organizations to have a comprehensive understanding of all the domains associated with their network, enabling better visibility into potential attack vectors.
- Better security posture: By identifying and securing these subdomains, organizations can effectively reduce their attack surface and minimize the chances of unauthorized access or compromise.
Actionable steps:
- Conduct a comprehensive DNS scan: Use tools like DNS enumeration or subdomain scanning to identify all the subdomains associated with a specific domain.
- Assess and prioritize risks: Once the subdomains are identified, prioritize them based on their potential impact and vulnerability. Focus on securing high-risk subdomains first.
- Regularly review and update subdomains: As new subdomains may be added or existing ones removed, it is crucial to continually review and update the list of identified subdomains to maintain an
Links:
Port Scanning
Port scanning is a technique used by attackers to identify open ports on a target system. By scanning different ports, attackers can gather information about potential vulnerabilities in a network or system.
Benefits:
- Identify open ports and potential vulnerabilities
- Evaluate network or system security
Actionable Steps:
- Regularly conduct port scans to identify any open ports that could be used as an entry point for attackers
- Implement port filtering or firewall rules to restrict access to only necessary ports and services
Links:
Web Application Firewalls
A web application firewall (WAF) is a security tool designed to protect web applications from various attacks, including SQL injection, cross-site scripting (XSS), and other vulnerabilities. It acts as a shield between the web application and the internet, monitoring and filtering incoming traffic to identify and block malicious requests.
Benefits:
- Enhanced security: WAFs provide an additional layer of protection to web applications, preventing common attacks and vulnerabilities.
- Improved performance: By filtering out malicious traffic before it reaches the application, WAFs can help optimize performance and reduce the load on the server.
Actionable steps:
- Evaluate and choose a WAF solution: Research and select a reputable web application firewall provider that suits your requirements.
- Configure the WAF rules: Customize the firewall rules according to the specific needs of your web application, considering potential threats and vulnerabilities.
- Regularly update and monitor the WAF: Keep the WAF up to date with the latest security patches and continuously monitor alerts and logs for any signs of suspicious activity.
- Setup Cloudflare Access / Zero Trust for admin panels and non public tools
Links:
Source Code Security
| Info | Advice |
|---|---|
 |  |
Branch protections
Branch protections on services such as Github and Gitlab allow repository administrators to enforce certain rules and restrictions on specific branches within a repository. These protections help maintain the integrity and security of the codebase, as well as facilitate collaboration among developers.
Benefits:
- Prevent accidental changes: Branch protections can prevent force pushes, which helps safeguard against accidental data loss or overwriting of code.
- Enforce code quality: By requiring certain checks, such as passing tests or successful code review, branch protections ensure that only verified and high-quality code is merged into protected branches.
Actionable steps:
- Define required status checks: Specify the checks that need to pass before merging into the protected branch, such as code reviews or successful tests and linting, to enforce code quality.
- Set up branch protection rules: Configure other restrictions like preventing force pushes, requiring certain reviewers, or requiring signed commits to maintain code integrity and enforce security protocols.
Links:
Commit signing
Commit signing refers to the process of adding a digital signature to software code commits in order to ensure their integrity and authenticity. It involves using cryptographic techniques to generate a unique signature that can be verified to prove that the commit has not been tampered with and was made by a trusted source.
Benefits:
- Integrity verification: Commit signing ensures that the code commits have not been modified or manipulated during the development process.
- Authentication: It provides assurance that the commit was made by a trusted individual or organization.
Actionable steps:
- Generate keys: Create a pair of PGP keys (private and public) to be used for signing commits.
-
Sign commits: Use the private key to generate a unique signature for each commit, and add it to the commit message or metadata.
- Github: Commit signature verification
Dependencies
DDependency monitoring with tools like Snyk and Dependabot refers to the practice of continuously monitoring the dependencies used in an application or software project for any known security vulnerabilities or other issues, and taking proactive measures to address them.
Benefits:
- Early detection of vulnerabilities: Dependency monitoring helps to identify and address vulnerabilities in the dependencies before they can be exploited by attackers.
- Saves time and effort: These tools automate the process of checking for vulnerabilities, saving the developers’ time and effort in manually reviewing dependencies.
Actionable steps:
- Set up dependency monitoring tools: Install and configure tools like Snyk or Dependabot to automatically scan and monitor the dependencies in your project.
- Regularly update dependencies: Keep your dependencies up to date by regularly checking for and applying updates that include security patches and fixes.
- Address vulnerabilities: When a vulnerability is identified, take prompt action by updating or replacing the affected dependency with a secure version to mitigate the risk.
Links:
SAST
SAST stands for Static Application Security Testing. It is a type of security testing that involves analyzing the source code of an application to identify vulnerabilities and potential security weaknesses.
Benefits of SAST:
- Early detection of vulnerabilities: SAST helps in identifying security flaws in the source code during the development phase, allowing for timely remediation before the application is deployed.
- Automates security testing: SAST tools can automatically scan and analyze the source code, reducing the manual effort required for security testing.
Actionable steps for implementing SAST:
- Select a suitable SAST tool: Research and choose a SAST tool that can analyze the programming languages and frameworks used in the application.
- Configure and scan the source code: Configure the SAST tool to scan the source code of the application for potential vulnerabilities.
- Analyze the results: Review the SAST scan results to identify security vulnerabilities and prioritize them for remediation.
Links:
Logging & Error Monitoring
Logging and error monitoring is the process of collecting and analyzing logs and error messages generated by various systems, applications, and devices to identify and rectify any issues or anomalies that may indicate potential security threats or system vulnerabilities.
Benefits:
- Early detection of security incidents or breaches
- Proactive identification and resolution of system errors and bugs to minimize downtime and improve stability
Actionable steps:
- Implement a centralized logging system to aggregate logs from various sources.
- Configure automated notifications for critical errors or security-related events.
- Regularly review logs and error messages to spot any unusual activities or patterns.
Links:
Application Security
| Info | Advice |
|---|---|
 |  |
HSTS
HSTS stands for HTTP Strict Transport Security. It is a security feature that helps protect websites against certain types of attacks, such as SSL stripping and man-in-the-middle attacks. When a website has HSTS enabled, it tells the user’s browser to only access the website over a secure HTTPS connection, even if the user types in “http://” in the address bar.
Benefits of HSTS:
- Protects against SSL stripping attacks and man-in-the-middle attacks
- Helps ensure that website communication is always encrypted and secure
Actionable steps to enable HSTS:
- Configure your web server or web application to send the “Strict-Transport-Security” header with a specified max-age value greater than 6 months.
- Ensure that your web server supports HTTPS and has a valid SSL/TLS origin certificate installed.
Links:
Cookies
Cookie attributes such as Secure, HttpOnly, Path, Domain, and expiry are important features in web security to protect user information and prevent unauthorized access to cookies.
Benefits:
- Secure attribute ensures that cookies are only transmitted over secure HTTPS connections, protecting the information from interception.
- HttpOnly attribute prevents client-side scripts from accessing the cookie, reducing the risk of cross-site scripting (XSS) attacks.
Actionable Steps:
- Set the Secure attribute on cookies to ensure they are only transmitted over HTTPS connections.
- Add the HttpOnly attribute to cookies to prevent client-side scripts from accessing them.
- Use the Path attribute to restrict the cookie to specific paths on your website, further enhancing security.
- Use the Domain attribute to limit the cookie to a specific subdomain or set of domains, preventing unauthorized access.
- Set an appropriate expiry time for cookies to control their lifespan and minimize the risk of data exposure.
Links:
Session Management
Session management refers to the process of maintaining and tracking the various sessions or interactions between a user and a system or website. It involves creating, maintaining, and terminating sessions to ensure secure and seamless user experience.
Benefits of session management:
- Enhanced security: Session management helps prevent unauthorized access by implementing measures like session timeouts, session tokens, and secure cookie management.
- Improved user experience: It allows users to have uninterrupted interactions with the system or website, with features like session resumption and session recovery.
Actionable steps for session management:
- Implement session timeouts: Configure the system to automatically terminate sessions after a predetermined period of inactivity to reduce the risk of unauthorized access.
- Use secure session tokens: Generate and assign unique session tokens to each user to prevent session hijacking and ensure secure communication between the user and the system.
- Encrypt session data: Protect sensitive session information by encrypting it both in transit and at rest, using strong encryption algorithms and secure protocols.
- Monitor and log session activities: Keep track of session events, such as login and log out attempts, session creations, and terminations, to detect any suspicious or unauthorized activities.
- Provide users with notice and control: Ensure users are notified of new sessions that from differing IPs and user agents, provide them with the ability to terminate other sessions.
Links:
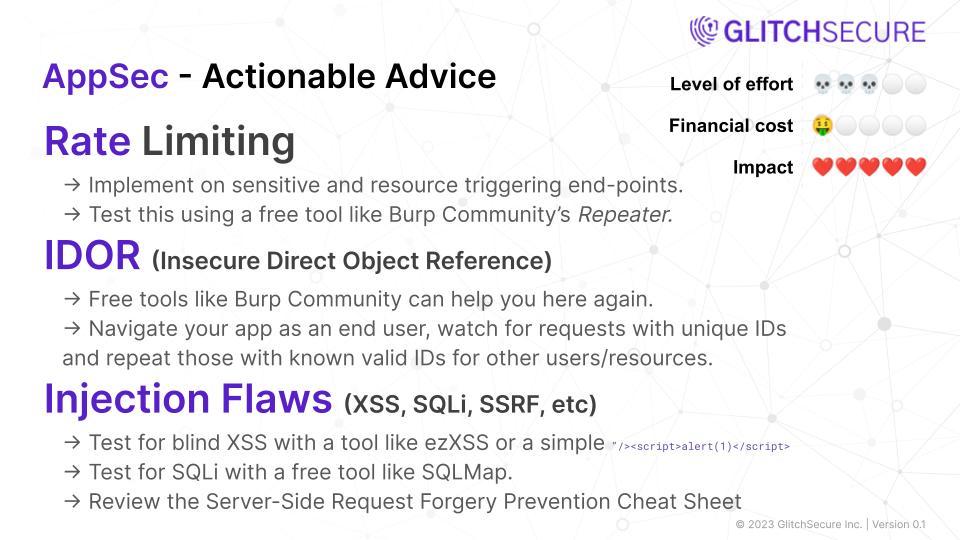
Rate Limiting
Rate Limiting is a technique used to control and limit the number of requests or actions made to a system or network within a certain time frame. It is employed to prevent abuse, protect against DDoS attacks, and ensure fair usage of resources.
Benefits of Rate Limiting:
- Prevents attacks on third party system resources such as email generation.
- Reduces impact of bruteforcing and information disclosure issues.
- Prevents denial of service through resource consumption.
Actionable steps for implementing Rate Limiting:
- Set sensible limits: Determine the appropriate maximum number of requests that can be made within a given time frame for each user or application.
- Implement rate limiting mechanisms: Utilize technologies like web application firewalls, framework specific limits, load balancers, or API gateways that enable rate limiting and configure them to enforce the desired limits. Utilize these in conjunction with one another.
Links:
IDOR
IDOR stands for Insecure Direct Object Reference, which refers to a vulnerability in web applications where an attacker can access unauthorized resources or perform unauthorized actions by manipulating direct object references. This vulnerability arises when an application does not properly enforce access controls on the direct object references it exposes.
Benefits:
- Improved data protection: By addressing IDOR vulnerabilities, sensitive data and resources can be better protected from unauthorized access and exploitation.
- Enhanced user trust: Fixing IDOR vulnerabilities demonstrates a commitment to security, helping to build trust with users and customers.
Actionable Steps:
- Implement appropriate access controls: Ensure that access controls are implemented and enforced properly throughout the application to prevent unauthorized access to resources.
- Use indirect references: Avoid directly referencing sensitive resources or data in URLs or other client-side parameters. Instead, use indirect references that are harder to guess or tamper with.
Links:
Injection Flaws
Injection flaws, such as SQLi (SQL Injection), XSS (Cross-Site Scripting), and SSRF (Server-Side Request Forgery), are vulnerabilities that allow an attacker to manipulate input data to execute arbitrary commands or inject malicious code into an application’s database, client-side scripts, or server-side requests. These flaws can lead to unauthorized access, data breaches, and compromise of sensitive information.
Benefits of addressing injection flaws:
- Enhanced security posture: Mitigating injection flaws helps protect against various attacks, preventing unauthorized access and potential data breaches.
- Secure application development: By addressing injection flaws, organizations can follow secure coding practices and ensure the security of their applications.
Actionable steps to address injection flaws:
- Implement input validation: Validate all user input to ensure it adheres to the expected format and meets predefined criteria, such as type, length, and character restrictions.
- Employ parameterized queries and prepared statements: Use parameterized queries or prepared statements in database access to separate SQL code from user input, preventing SQLi attacks.
- Implement output encoding and validation: Properly escape or sanitize user-generated content before rendering it on the client-side to prevent XSS attacks.
- Restrict server-side requests: Validate and sanitize all external requests made by the
Links:
Security Testing
| Info | Advice |
|---|---|
 | 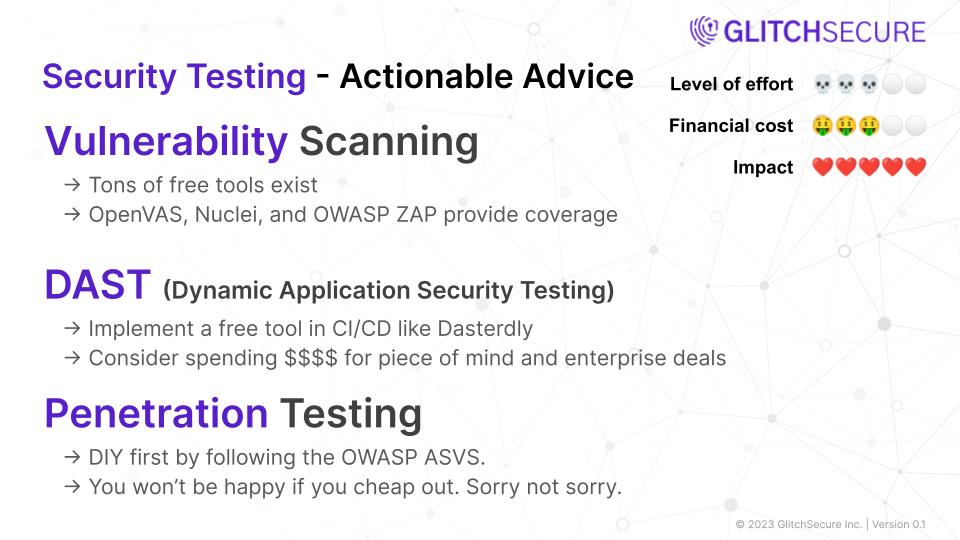 |
Vulnerability Scanning
Vulnerability scanning is the process of identifying and analyzing vulnerabilities in computer systems, networks, and software applications. It is a proactive approach to identify potential weaknesses that can be exploited by attackers. Vulnerability scans typically rely on fingerprinting in order to determine if a vulnerability may reasonability exist.
Benefits:
- Helps identify potential publicly known vulnerabilities before they can be exploited by attackers
Actionable steps:
- Conduct regular vulnerability scans using automated scanning tools
- Establish a process to track and prioritize vulnerabilities based on their criticality
- Implement appropriate patches or remediation measures for identified vulnerabilities
Links:
DAST
Dynamic Application Security Testing (DAST) is a security testing methodology that assesses the security of web applications by sending requests and analyzing the responses in real-time. It helps identify vulnerabilities in the application code, configurations, and server-side components from the perspective of an external attacker.
Benefits of DAST:
- Identifies security vulnerabilities in real-time during the application’s runtime.
- Provides an accurate representation of how the application behaves in a live environment.
Actionable steps for DAST:
- Use a DAST tool to scan the web application and identify potential vulnerabilities.
- Analyze the scan results to prioritize and address the identified security issues.
- Regularly perform DAST scans to ensure ongoing security of the application.
Links:
Penetration Testing
Penetration testing, is a security assessment technique that involves simulating real-world attacks to identify vulnerabilities in a system or network. It is performed by trained professionals who attempt to exploit weaknesses and gain unauthorized access, giving organizations an opportunity to identify and resolve security issues before malicious hackers can exploit them.
Benefits:
- Identifies vulnerabilities in systems and networks that could be exploited by malicious actors.
- Helps organizations understand their security weaknesses and prioritize remediation efforts.
Actionable steps:
- Define the scope and objectives of the penetration test.
- Conduct a thorough reconnaissance to gather information about the target.
- Identify and exploit vulnerabilities to gain unauthorized access.
-
Document and report findings, including recommended remediation steps.
- OWASP ASVS
- OWASP Testing Guide
- GlitchSecure Real-time Penetration Testing
Vulnerability Reports
| Info | Advice |
|---|---|
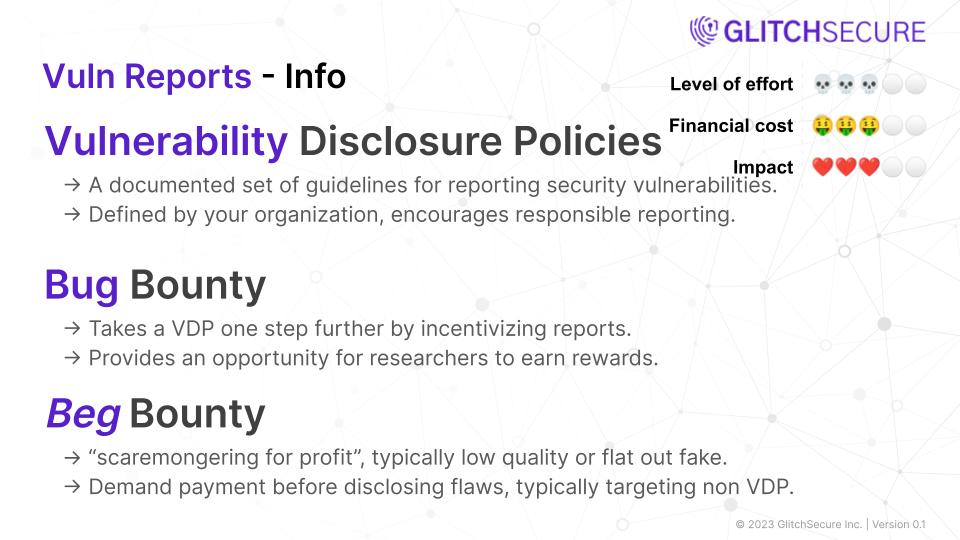 |  |
Vulnerability Disclosure Policies
Vulnerability disclosure policy refers to a documented set of guidelines and procedures for reporting security vulnerabilities in software or systems to the organization responsible for maintaining them. It defines how individuals can responsibly disclose vulnerabilities they have discovered and how the organization will respond to and remediate those vulnerabilities.
Benefits:
- Encourages responsible reporting: A vulnerability disclosure policy provides clear instructions for individuals to report vulnerabilities they have discovered rather than exploiting them or sharing them publicly.
- Improves security: By establishing a clear process for reporting vulnerabilities, organizations can receive timely and accurate information that helps them identify and fix security flaws before they are exploited by attackers.
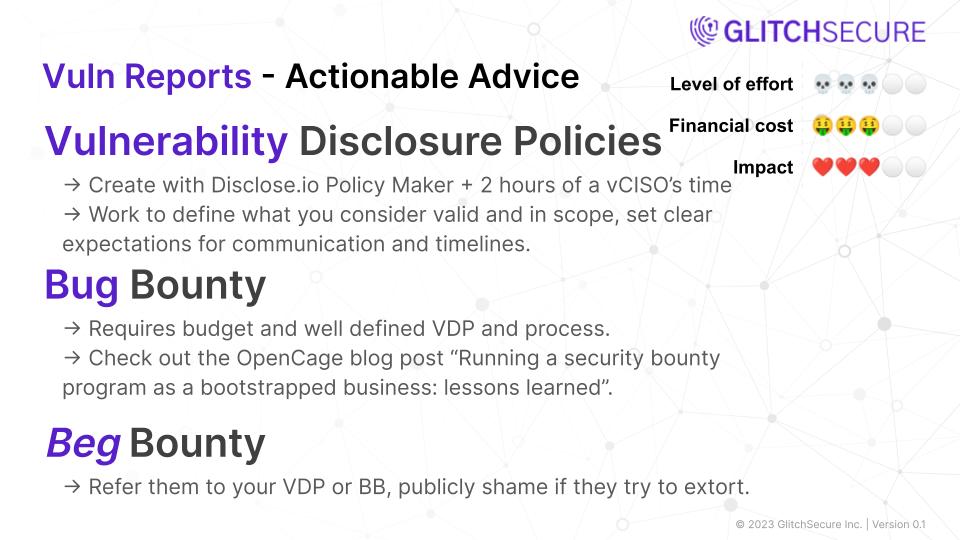
Actionable steps:
- Create a clear and comprehensive policy: Develop a vulnerability disclosure policy that outlines what vulnerabilities can be reported, how to report them, and how the organization will handle and respond to the reports.
- Establish a reporting channel: Provide a secure and easy-to-use mechanism for individuals to report vulnerabilities, such as a dedicated email address or an online form. Make sure to clearly communicate this reporting channel to potential reporters.
- Acknowledge and respond to reports: Ensure that you have a system in place to acknowledge receipt of vulnerability reports and provide regular updates on the progress of remediation efforts.
- Patch and disclose: Once a vulnerability has been reported and fixed,
Links:
Bug bounty
Bug bounty programs are initiatives offered by organizations to incentivize cybersecurity researchers to find and report vulnerabilities in their systems and software. These programs can be highly beneficial for companies, as they allow them to identify and fix vulnerabilities before they are exploited by malicious hackers. Additionally, bug bounty programs can help organizations improve their overall security posture and gain public trust. For researchers, bug bounty programs provide an opportunity to earn rewards for their skills and expertise.
Benefits:
- Early identification and mitigation of vulnerabilities
- Cost-effective compared to hiring full-time security experts
Actionable steps for organizations:
- Define clear goals and scope for the bug bounty program.
- Set up a process to triage and validate bug reports promptly.
Actionable steps for researchers:
- Familiarize yourself with the organization’s guidelines for testing and reporting vulnerabilities.
- Thoroughly document and provide clear evidence of any vulnerabilities you find.
Links:


